27 Sep How can you set up a proxy?
Download and install Tor from this link:
https://www.torproject.org/download/
Tor (The Onion Router) is a free, open-source software that enables anonymous communication on the internet by directing traffic through a worldwide, volunteer overlay network to conceal users’ location and usage from network surveillance or traffic analysis.
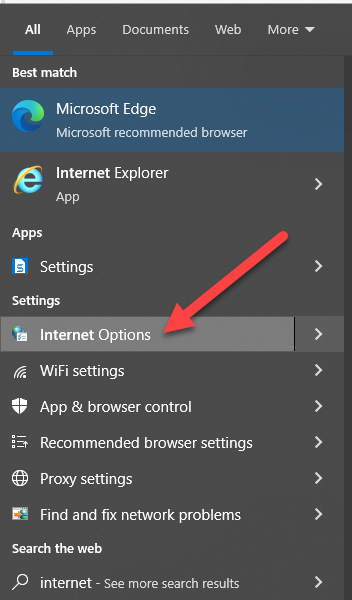
Click your windows start icon and type ‘Internet Options’:
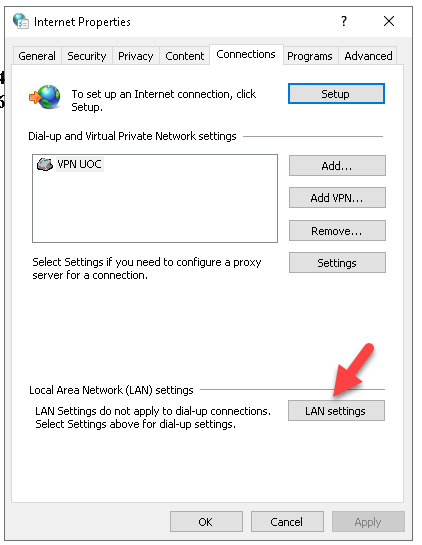
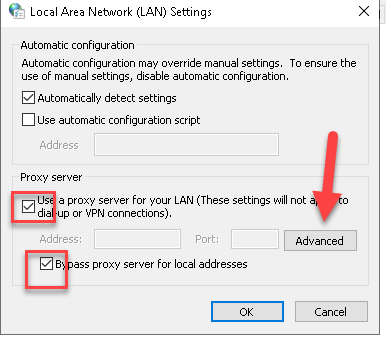
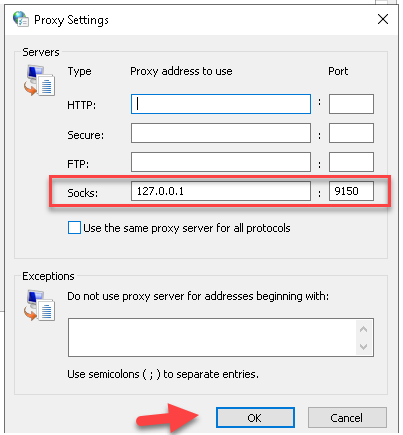
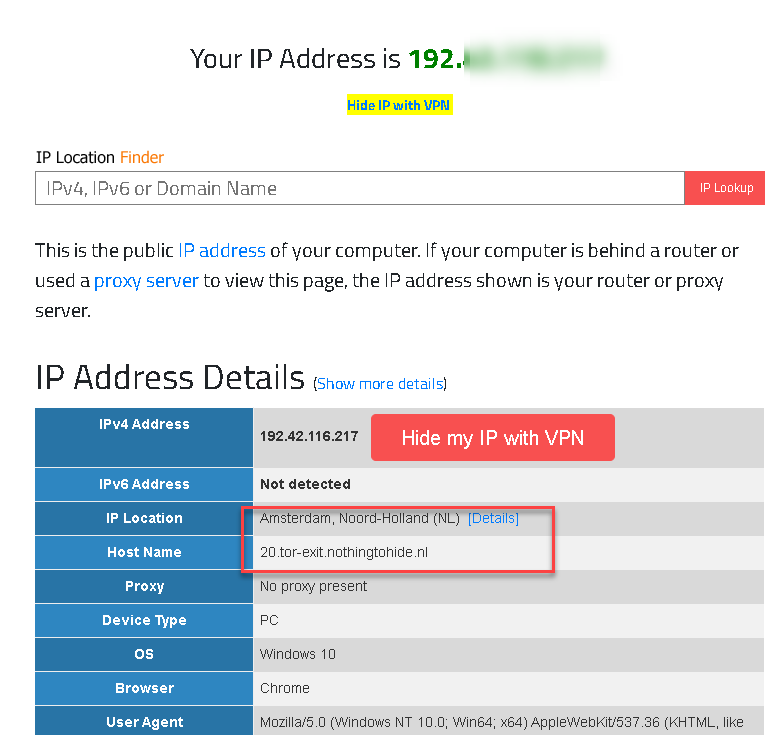
You can now reroute your internet traffic via TOR.
In Windows, the “Internet Options” control panel allows users to configure various settings related to browsing and internet connections. Among these settings is the ability to configure a proxy server. One type of proxy setting available is “SOCKS”.
SOCKS (Socket Secure) is a protocol that facilitates the routing of network packets between a client and a server through a proxy server. It can be used to bypass internet restrictions or provide a layer of anonymity.
- When you select the SOCKS option, you’re instructing your system to route its internet traffic through a SOCKS proxy server.
- You’d typically provide the IP address (or hostname) and the port number of the SOCKS proxy server you want to use.
Once configured, applications that respect the system’s proxy settings will direct their traffic through the specified SOCKS proxy. Note, however, that not all applications use these system settings by default, and some may require additional configuration or may not support SOCKS at all.







