synergy AUTO LOG OFF OPEN APPLICATIONS AND CONNECTIONS

The problem
 Hackers, often labeled as cyber criminals, are individuals or groups that infiltrate networks and digital devices without permission. Their typical aim revolves around obtaining confidential data, ranging from personal financial information to valuable business secrets, thereby threatening personal security and corporate integrity. This illicit access to sensitive data can lead to a multitude of detrimental consequences such as identity theft, financial losses, and corporate espionage.
Hackers, often labeled as cyber criminals, are individuals or groups that infiltrate networks and digital devices without permission. Their typical aim revolves around obtaining confidential data, ranging from personal financial information to valuable business secrets, thereby threatening personal security and corporate integrity. This illicit access to sensitive data can lead to a multitude of detrimental consequences such as identity theft, financial losses, and corporate espionage.
To mitigate such risks, multiple protective measures can be implemented. Firewalls and antivirus software are instrumental in creating a robust digital shield against these unauthorized infiltrations. Firewalls monitor and control incoming and outgoing network traffic based on predetermined security rules, thus acting as a barrier between a trusted network and untrusted networks. Antivirus software, on the other hand, helps protect your computer against most viruses, trojans, and other malicious software, providing an extra layer of security.
In addition to these technical safeguards, adherence to the best practices for computer use is equally essential. Many businesses, particularly those that operate servers, are often running at full capacity around the clock. This continual operation potentially increases the visibility of these systems, making them attractive targets for hackers.
Being continually logged on makes your system more susceptible to cyber attacks. Therefore, it is highly recommended to log off when not in use. This practice effectively breaks the connection a hacker may have established with your network, thereby interrupting any potential malicious activities. Notably, logging off also clears temporarily granted credentials to network shares, adding another layer of security by preventing unauthorized access to shared resources.
Moreover, when you log off, memory consumed by opened applications is reclaimed. This not only enhances the performance of your system but also reduces the likelihood of software vulnerabilities that could be exploited by hackers. Consequently, combining both active protective measures and informed usage practices provides a comprehensive defense against cyber threats.
The solution

Responding to our clients’ needs, we’ve created SynergyAutoLogOff, a Windows application engineered to automatically sign users out following a designated period of inactivity, enhancing security measures. This auto-sign-out feature ensures that all saved credentials are cleared, minimizing the possibility of unwarranted access.
It’s important to note that SynergyAutoLogOff is not intended to substitute for a screen saver.
Instead, it actively terminates any open applications and network connections, securely bringing the user back to the Login Screen.
Make sure to have your open data/documents saved!
The application operates in the background, silently monitoring user activity every time you power on your computer or sign in to a Windows user profile. This feature guarantees that the risk of forgetting to log off is eliminated, further enhancing the security of your system.
With SynergyAutoLogOff, not only does your system become less susceptible to potential intrusions, but it also ensures optimal performance by freeing up system resources that would otherwise be used by idle applications.
Hence, SynergyAutoLogOff adds a vital layer to your cybersecurity measures while improving system efficiency.
- Free and Open Source
- Simple to use
- No installation needed
Visual Tour
All the files you need are in the zip file
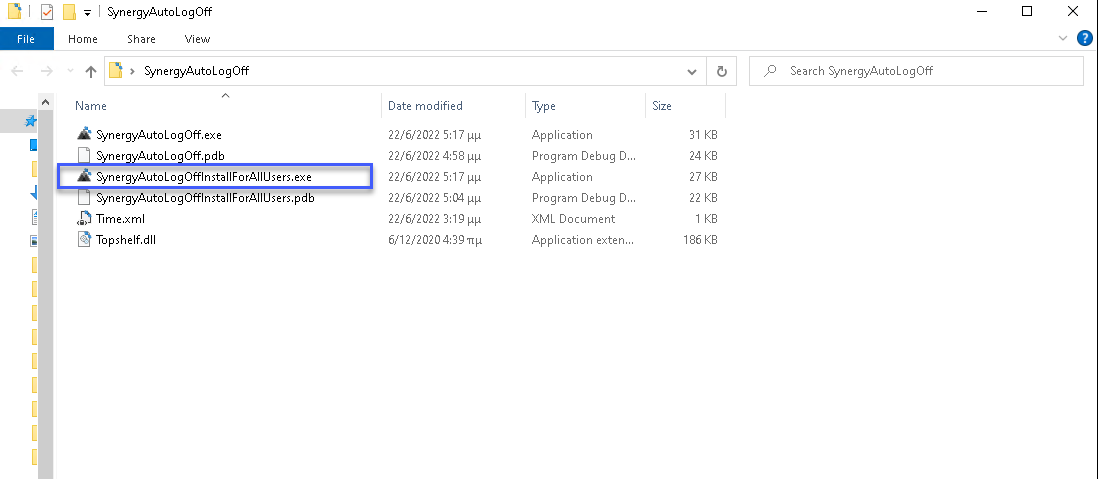
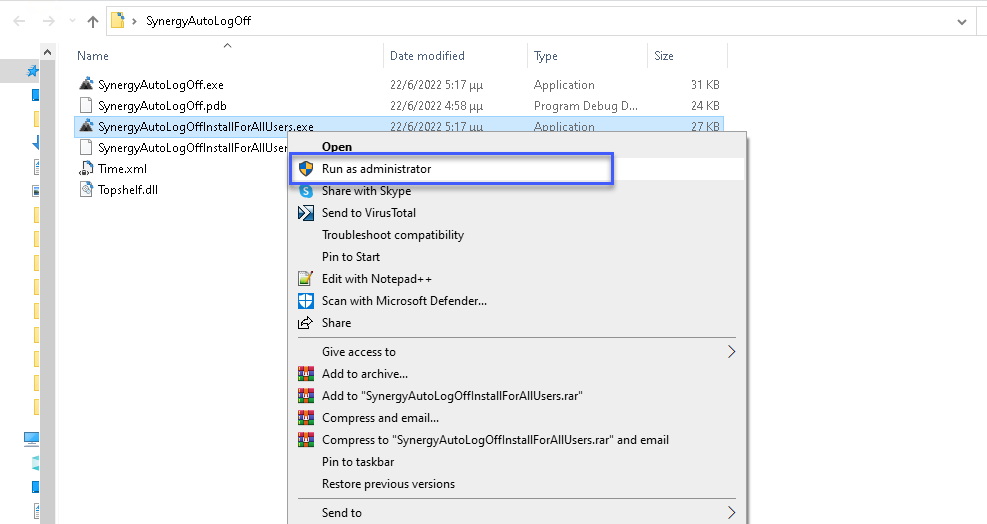
In order to install SynergyAutoLogOff Run As Administrator SynergyAutoLogOffInstallForAllUsers.exe
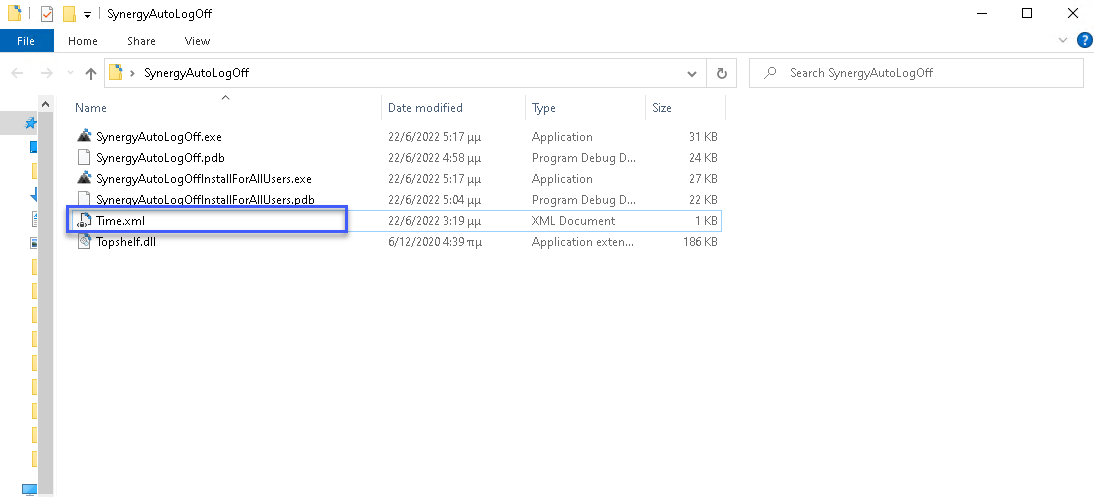
In order to set the minutes of inactivity you want to log off edit Time.xml file
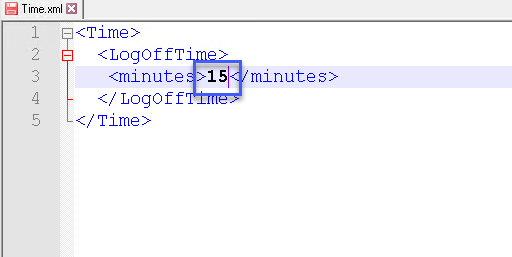
Change the number as shown in the image below and save the file
Set your desired Inactivity time and then log off and re-login to have the application started working.
Get the solution
![]() Every application we build has been checked for Mailware by VirusTotal. See the scan results
Every application we build has been checked for Mailware by VirusTotal. See the scan results









