
04 Nov How to connect/remote Hyper-V Server using Server Manager from another Windows Server and view Task Scheduler
First we have to enable communication between the two servers.
Connect to your Hyper-V Server and open powershell. Type the following two commands:
Enable-PSRemoting
Enable-WSManCredSSP -Role server
From your Windows Server that will remotely manage your Hyper-V start a powershell and type the following commands. Replace the name in quotes with your Hyper-V Server name.
Set-Item WSMan:\localhost\Client\TrustedHosts -Value "Replace with your Hyper-V Name"
Enable-WSManCredSSP -Role client -DelegateComputer "Replace with your Hyper-V Name"
From your Windows Server start the Server Manager, add the Server as usual and select.
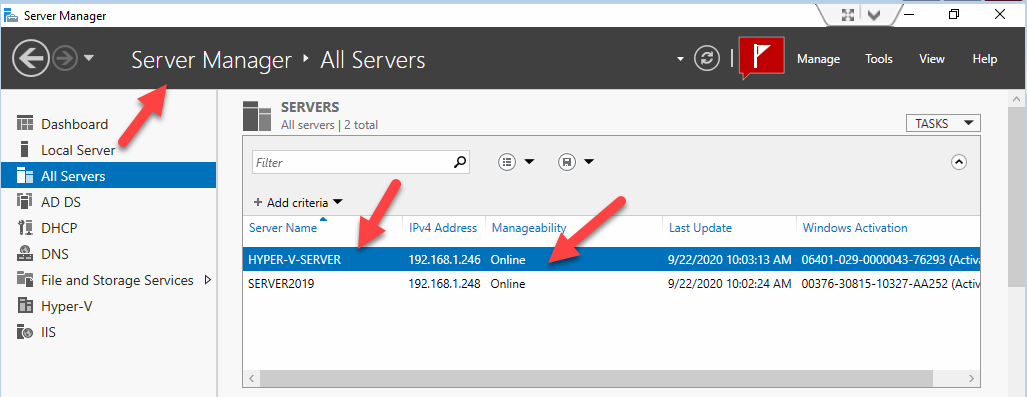
Right click over the Server and click “Manage As…”
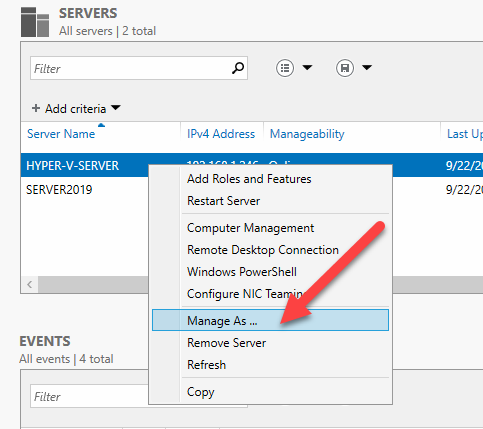
Type your Hyper-V’s credentials
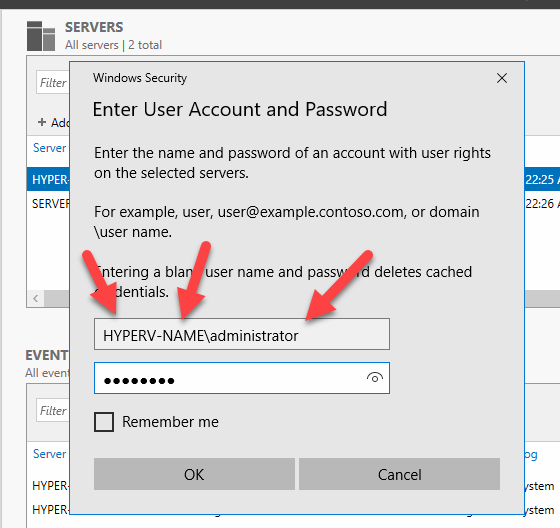
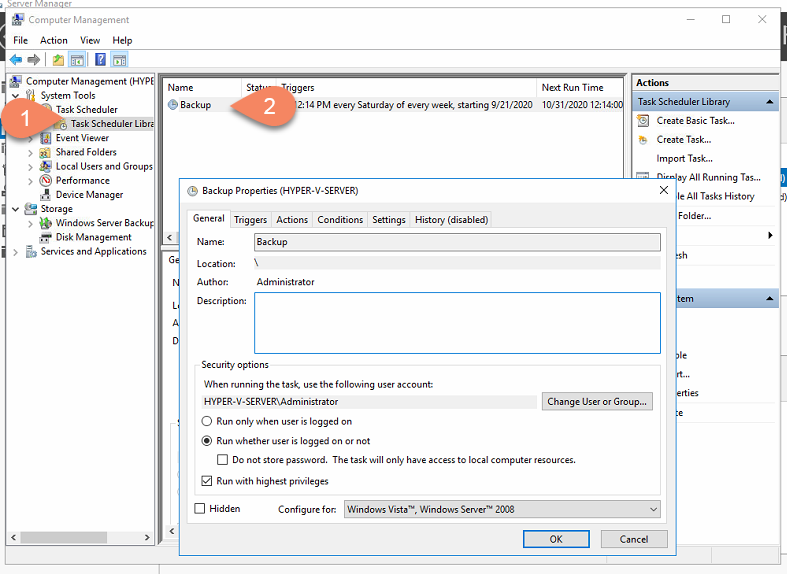
Start Computer Management on the remote Hyper-V Server.
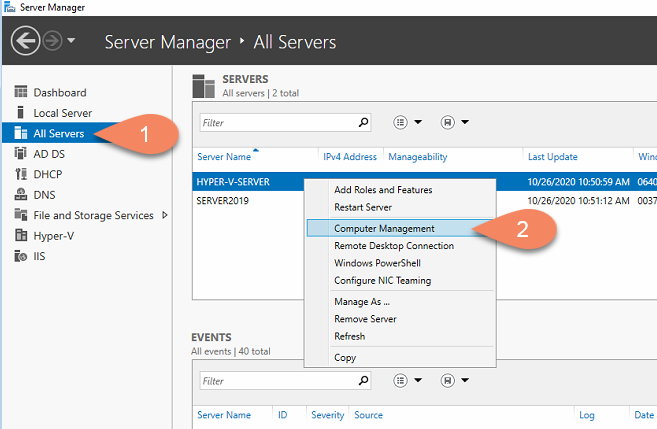
You are now able to View/Edit Task Schedules on the remote Hyper-V Server
latest posts
Automate Creation of Serial Numbers In An Existing PDF Template
We received a request from a client, to automate the creation of Serial Numbers inside a PDF file.The PDF was a A3+ format and was designed in such a way...
Are you moving away from VMware due to the new pricing method ? – Why not test Microsoft free Hyper-V as a VMware alternative
Since 2010, we've been using Hyper-V, starting from its 2008 version. Hyper-V essentially operates as a Windows Server Core, without a Graphics User Interface, and we deploy it as a...
Seven + 1 Effective Measures for Cybersecurity in Businesses
Cyberattacks are a big risk for all businesses, big and small. They can disrupt how things run and may cause a loss of money and customers. If a company's cybersecurity...
Unveiling Hidden Dangers: The Perils of UPnP and Protecting Your Digital Homestead – Apple Time Capsule
The Dangers of Default Settings: A Narrative on UPnP and Data Vulnerability During one of my routine client visits, I encountered a situation that underscored the criticality of cybersecurity in...









