24 Mar Hafnium Hack – How to run the patches, with simple detailed instructions.
Why make such a “How to”?
Because all articles we found so far, talk about what to do, but none shows how to do it.
So let’s start.
1. HOW TO KNOW IF YOU ARE “INFECTED”
Download the “Test-ProxyLogo n.ps1” script from the following Microsoft link: https://github.com/microsoft/CSS-Exchange/tree/main/Security
Open your “Exchange Management Shell” ((click on the magnifying glass on the lower left corner of your screen and type the name)
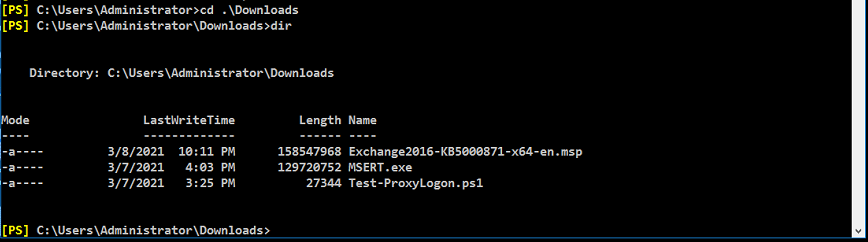
Change to the Downloads path using the CD command:
cd c:\users\administrator\downloads
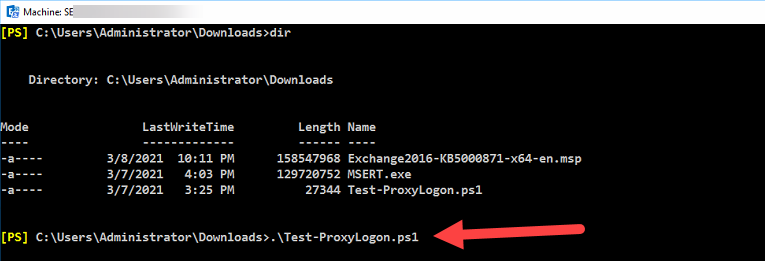
To run the script you have to type:
.\Test-ProxyLogon.ps1
A clean server looks like the one below:
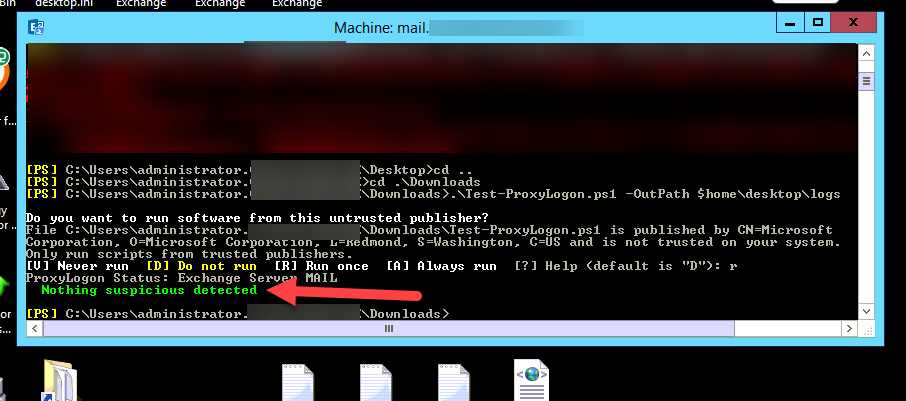
An “infected” server looks like the one below:
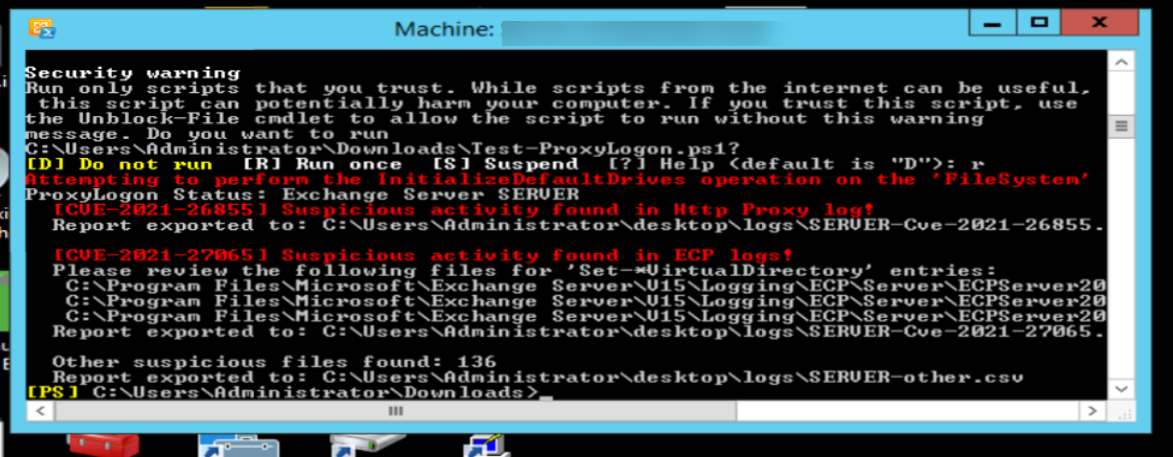
2. INSTALL THE LATEST CU
Before you can apply the “.msb” patch you need to have the latest CU already installed!
In case it is not installed you will get the following:
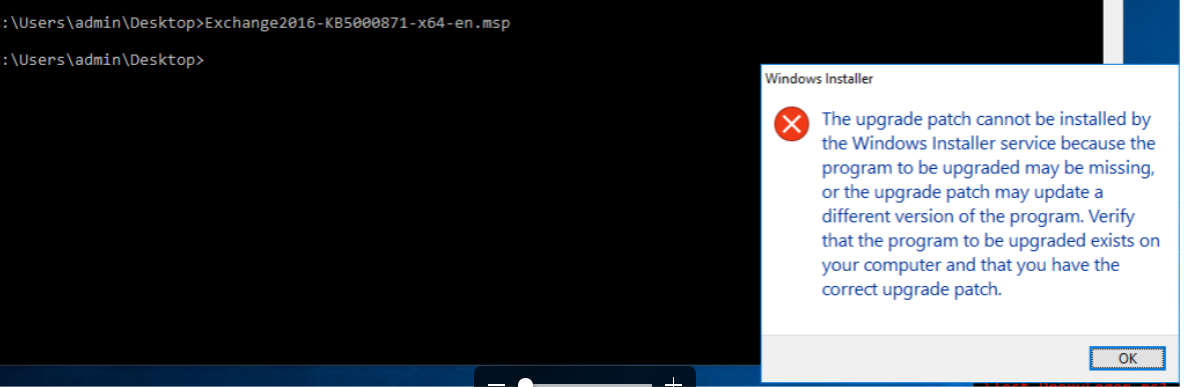
(Yes, it’s not clear. You might think you are doing something wrong with running the patch.)
First let’s see how you can find which CU (Cumulative Update) you have installed:
Back in the “Exchange Management Shell” type the following command:
Get-ExchangeServer | fl Name, Edition, AdminDisplayVersion
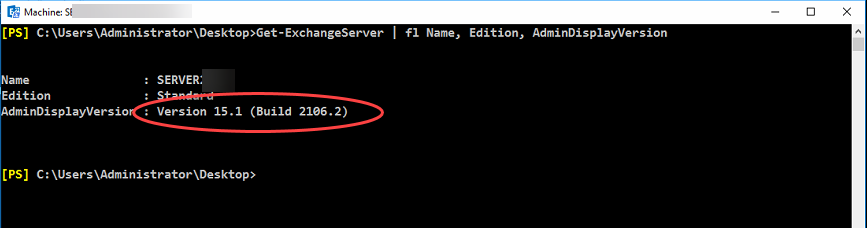
Check Version and Build from the list below:
Exchange 2010
14.3.123.4 = Microsoft Exchange Server 2010 SP3
Exchange 2013
15.0.620.29 = Exchange Server 2013 Cumulative Update 1 (CU1)
15.0.712.24 = Exchange Server 2013 Cumulative Update 2 (CU2)
15.0.775.38 = Exchange Server 2013 Cumulative Update 3 (CU3)
15.0.847.32 = Exchange Server 2013 Service Pack 1 (CU4)
15.0.913.22 = Exchange Server 2013 Cumulative Update 5 (CU5)
15.0.995.29 = Exchange Server 2013 Cumulative Update 6 (CU6)
15.0.1044.25 = Exchange Server 2013 Cumulative Update 7 (CU7)
15.0.1076.9 = Exchange Server 2013 Cumulative Update 8 (CU8)
15.0.1104.5 = Exchange Server 2013 Cumulative Update 9 (CU9)
15.0.1130.7 = Exchange Server 2013 Cumulative Update 10 (CU10)
15.0.1156.6 = Exchange Server 2013 Cumulative Update 11 (CU11)
15.0.1178.4 = Exchange Server 2013 Cumulative Update 12 (CU12)
15.0.1210.3 = Exchange Server 2013 Cumulative Update 13 (CU13)
15.0.1236.3 = Exchange Server 2013 Cumulative Update 14 (CU14)
15.0.1263.5 = Exchange Server 2013 Cumulative Update 15 (CU15)
15.0.1293.2 = Exchange Server 2013 Cumulative Update 16 (CU16)
15.0.1320.4 = Exchange Server 2013 Cumulative Update 17 (CU17)
15.0.1347.2 = Exchange Server 2013 Cumulative Update 18 (CU18)
15.0.1365.1 = Exchange Server 2013 Cumulative Update 19 (CU19)
15.0.1367.3 = Exchange Server 2013 Cumulative Update 20 (CU20)
15.0.1395.4 = Exchange Server 2013 Cumulative Update 21 (CU21)
15.0.1473.3 = Exchange Server 2013 Cumulative Update 22 (CU22)
15.0.1497.2 = Exchange Server 2013 Cumulative Update 23 (CU23)
Exchange 2016
15.1.396.30 = Exchange Server 2016 Cumulative Update 1 (CU1)
15.1.466.34 = Exchange Server 2016 Cumulative Update 2 (CU2)
15.1.544.27 = Exchange Server 2016 Cumulative Update 3 (CU3)
15.1.669.32 = Exchange Server 2016 Cumulative Update 4 (CU4)
15.1.845.34 = Exchange Server 2016 Cumulative Update 5 (CU5)
15.1.1034.26 = Exchange Server 2016 Cumulative Update 6 (CU6)
15.1.1261.35 = Exchange Server 2016 Cumulative Update 7 (CU7)
15.1.1415.2 = Exchange Server 2016 Cumulative Update 8 (CU8)
15.1.1466.3 = Exchange Server 2016 Cumulative Update 9 (CU9)
15.1.1531.3 = Exchange Server 2016 Cumulative Update 10 (CU10)
15.1.1591.10 = Exchange Server 2016 Cumulative Update 11 (CU11)
15.1.1713.5 = Exchange Server 2016 Cumulative Update 12 (CU12)
15.1.1779.2 = Exchange Server 2016 Cumulative Update 13 (CU13)
15.1.1847.3 = Exchange Server 2016 Cumulative Update 14 (CU14)
15.1.1913.5 = Exchange Server 2016 Cumulative Update 15 (CU15)
15.1.1979.3 = Exchange Server 2016 Cumulative Update 16 (CU16)
15.1.2044.4 = Exchange Server 2016 Cumulative Update 17 (CU17)
15.1.2106.2 = Exchange Server 2016 Cumulative Update 18 (CU18)
15.1.2176.2 = Exchange Server 2016 Cumulative Update 19 (CU19)
Exchange 2019
15.2.330.5 = Exchange Server 2019 Cumulative Update 1 (CU1)
15.2.397.3 = Exchange Server 2019 Cumulative Update 2 (CU2)
15.2.464.5 = Exchange Server 2019 Cumulative Update 3 (CU3)
15.2.529.5 = Exchange Server 2019 Cumulative Update 4 (CU4)
15.2.595.3 = Exchange Server 2019 Cumulative Update 5 (CU5)
15.2.659.4 = Exchange Server 2019 Cumulative Update 6 (CU6)
15.2.721.2 = Exchange Server 2019 Cumulative Update 7 (CU7)
15.2.792.3 = Exchange Server 2019 Cumulative Update 8 (CU8)
Search for the latest CU:

Download and run it:
Start the installation of the latest CU:
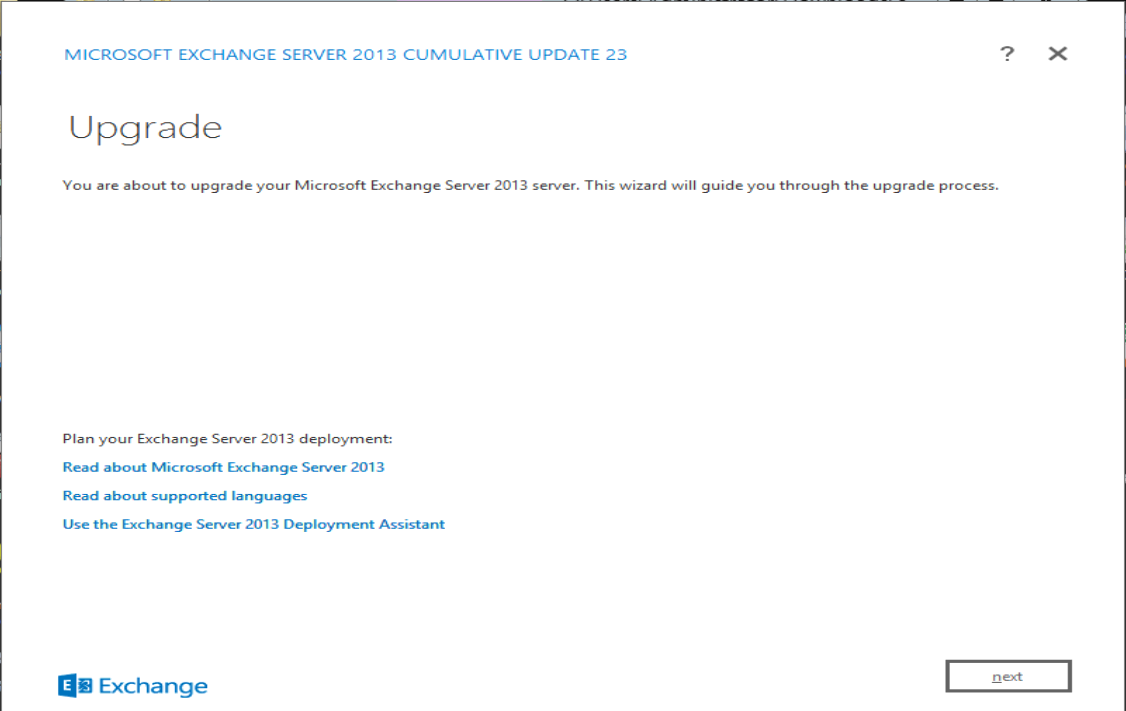
It will take a long time and you might need to install extra software like .Net and/or VC++ distributable files before running it. The window above will tell you what it needs.
3. run your Exchange patch
After the CU is installed then you can run your Exchange patch.
You can download it from Microsoft site: https://support.microsoft.com/en-us/topic/description-of-the-security-update-for-microsoft-exchange-server-2019-2016-and-2013-march-2-2021-kb5000871-9800a6bb-0a21-4ee7-b9da-fa85b3e1d23b

IMPORTANT: You need to open a command prompt as an Administrator.
This is how you can do it:
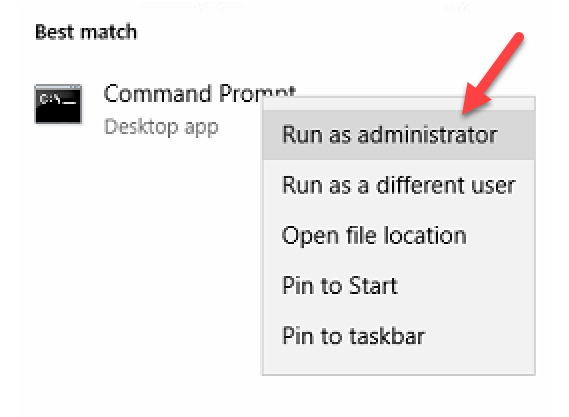
Search for the command prompt: (click on the magnifying glass on the lower left corner of your screen)
Right click over the command prompt and select the “Run as administrator”
Change to the Downloads folder:
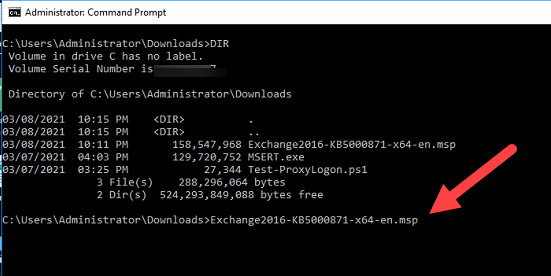
And type the name of your .msp patch: (ot type ‘ex’ and press the TAB key)
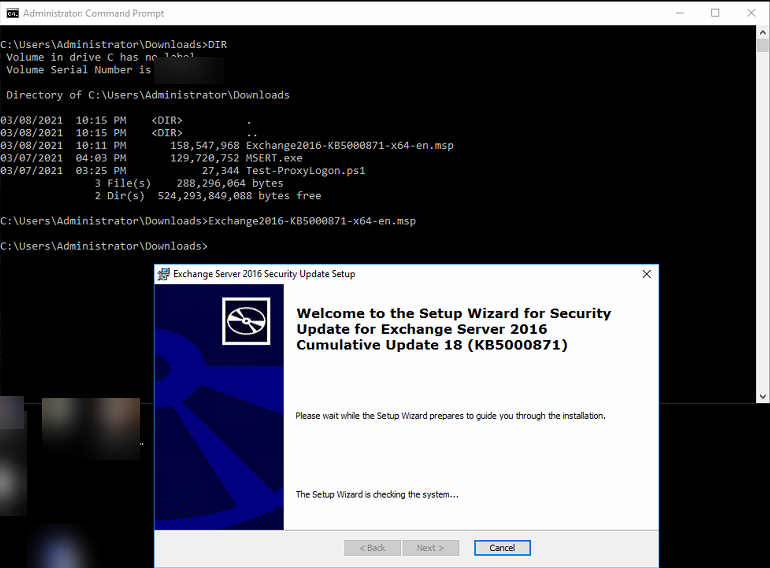
It will also take a long time to complete:
This is what you will get when finished:
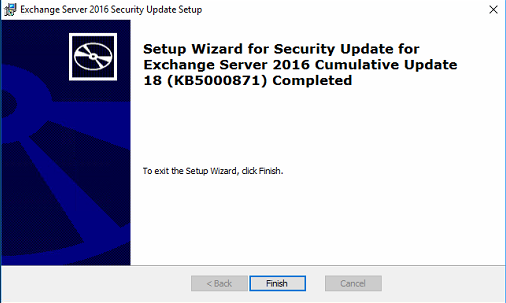
You are now patched!!!
In case you cannot install the latest CU or Patch, then at least run the Migitations (Anti Measures)
You can find them here: https://github.com/microsoft/CSS-Exchange/tree/main/Security
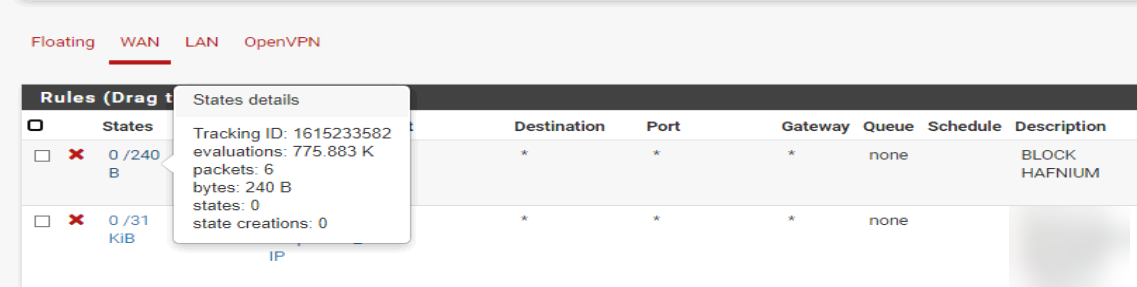
4. Block suspicious IPs
According to Cisa.gov, a number of servers were reported as suspicious: https://us-cert.cisa.gov/ncas/alerts/aa21-062a
103.77.192[.]219104.140.114[.]110104.250.191[.]110108.61.246[.]56149.28.14[.]163157.230.221[.]198167.99.168[.]251185.250.151[.]72192.81.208[.]169203.160.69[.]66211.56.98[.]1465.254.43[.]185.2.69[.]1480.92.205[.]8191.192.103[.]43
For extra security we decided to block the above IPs both for WAN and LAN traffic (incoming and outgoing connections) into our firewall.
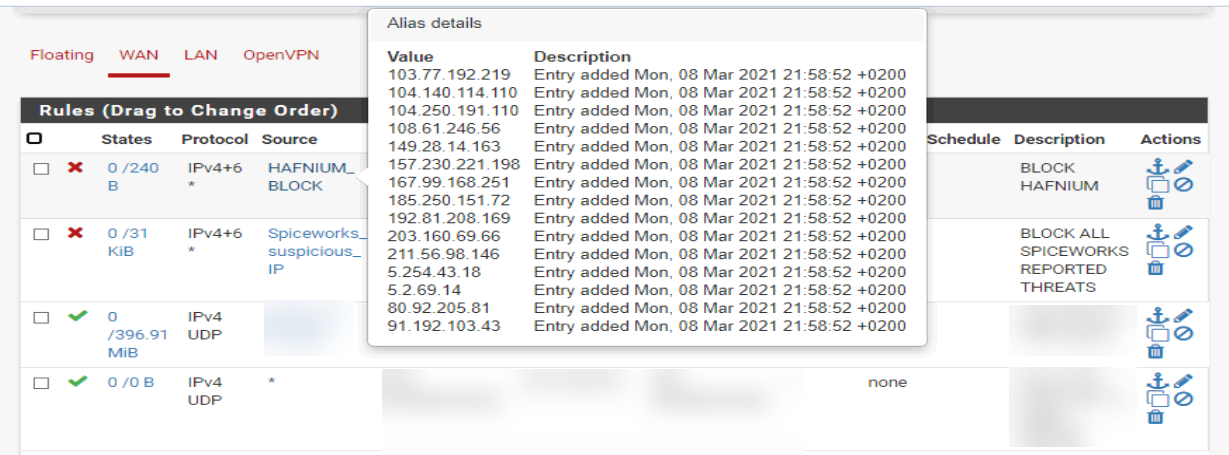
After some hours we noticed WAN traffic coming in from those IPs: It seems they tried to see if the Exchange server was still available for whatever they intended to do..